FreeDNS subdomains in anonymous proxy campaign
Jan 18, 2019
Do you use FreeDNS and get mysterious requests to attach to your domain? FreeDNS is a DNS hosting service that allows other users to add subdomains to your domains by default, conditional on your approval.
I receive many requests such as the following, but the destinations are always offline when I investigate. In these cases, these subdomains are briefly active from the time of creation until I delete them.
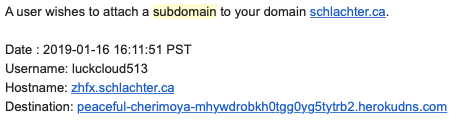
However, today I was requesting a Let's Encrypt certificate for a new subdomain that I had made for schlachter.ca, and surprisingly got a rate limiting error:
acme-client: transfer buffer: [{ "type": "urn:acme:error:rateLimited", "detail": "Error creating new cert :: too many certificates already issued for: schlachter.ca: see https://letsencrypt.org/docs/rate-limits/", "status": 429}] (204 bytes)
The limit is 50 certificates per domain per week (excluding renewals), and this week I haven't attempted to get any new certificates.
I hypothesized that my automatic renewal script might be requesting certificates too often, so I looked up all certificates for the domain and subdomains on a Certificate Transparency search page. Interestingly one subdomain dominated the results:
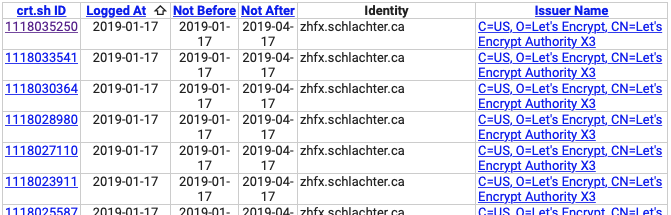
All in all, 182 certificates issued for zhfx.schlachter.ca! This is the same subdomain that a user had created on schlachter.ca earlier in the week. I assume many of the certificates listed are 'renewals' that don't count against the 50 certificates per domain per week.
Curiously, each of these certificates is for roughly 80 four-letter subdomains on a variety of domains:
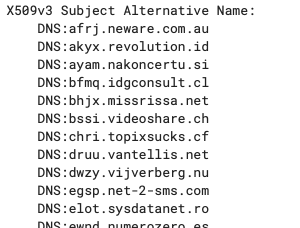
My first question was whether all of these domains using are also using FreeDNS, which is indeed the case:
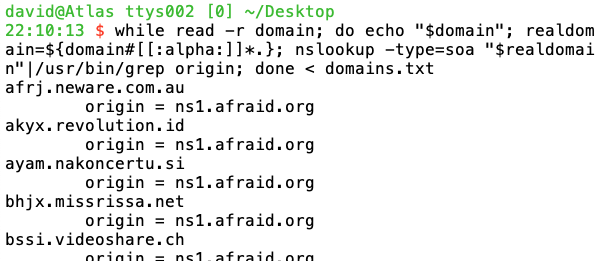
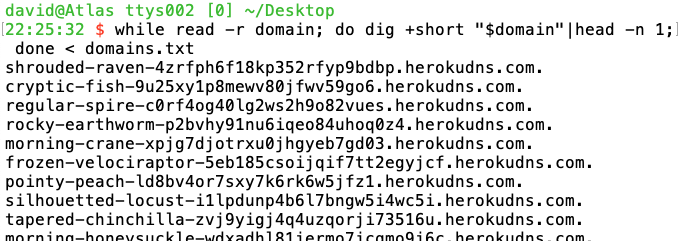
Where are these subdomains pointing? Those that resolve point to a variety of Heroku instances:
Are any of these subdomains online and offering any services? Here's a representative port scan with nmap.
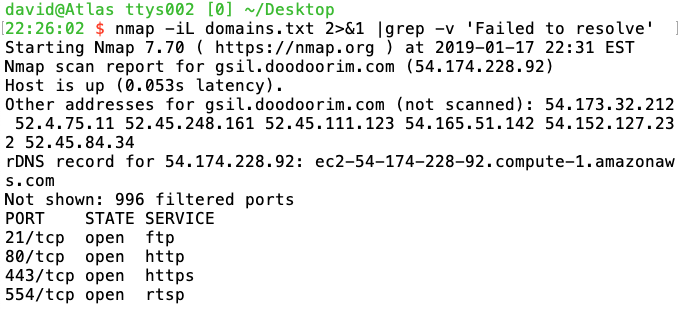
Every instance has four open ports: 21 (FTP), 80 (HTTP), 443 (HTTPS), and 554 (RTSP). A few have port 7070 (REAL Server?) open as well. Connection attempts on ports 21, 554, and 7070 all time out.
What's being served on port 80? Here are the titles and MD5 hashes of the pages hosted on the subdomains:
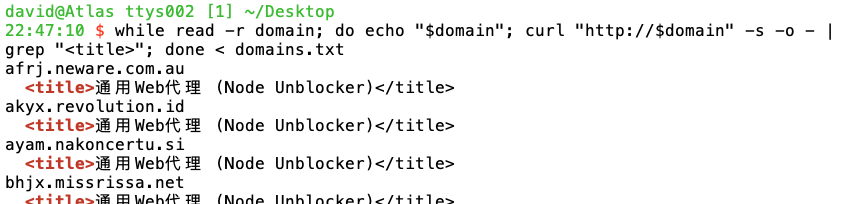
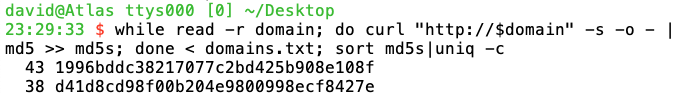
The pages all have the same title, and exist in two variants, as shown by the MD5 hashes. Ironically, none of the instances are accessible using TLS, despite the rate-limit-triggering certificate requests to Let's Encrypt.
What are these subdomains being used for? Here's a screenshot of one, as well as a Google Translate version of the same page translated to English:
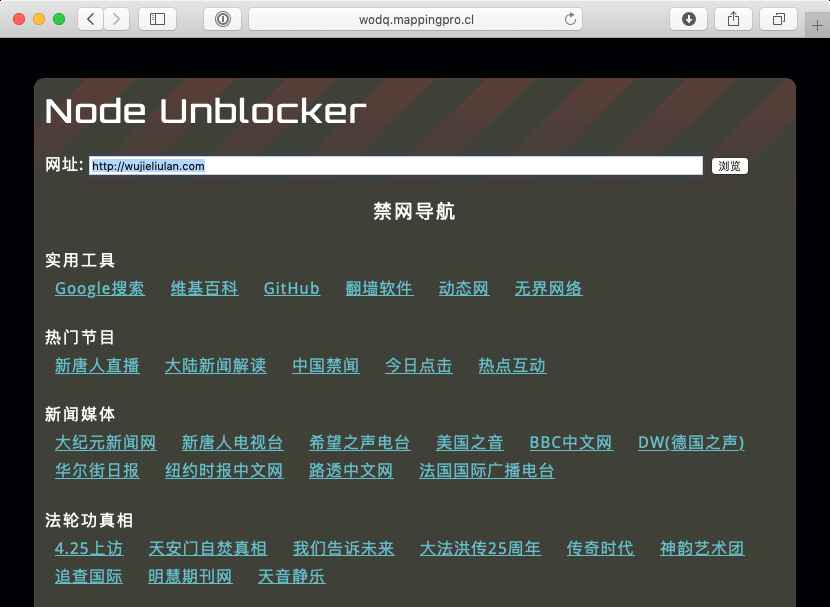
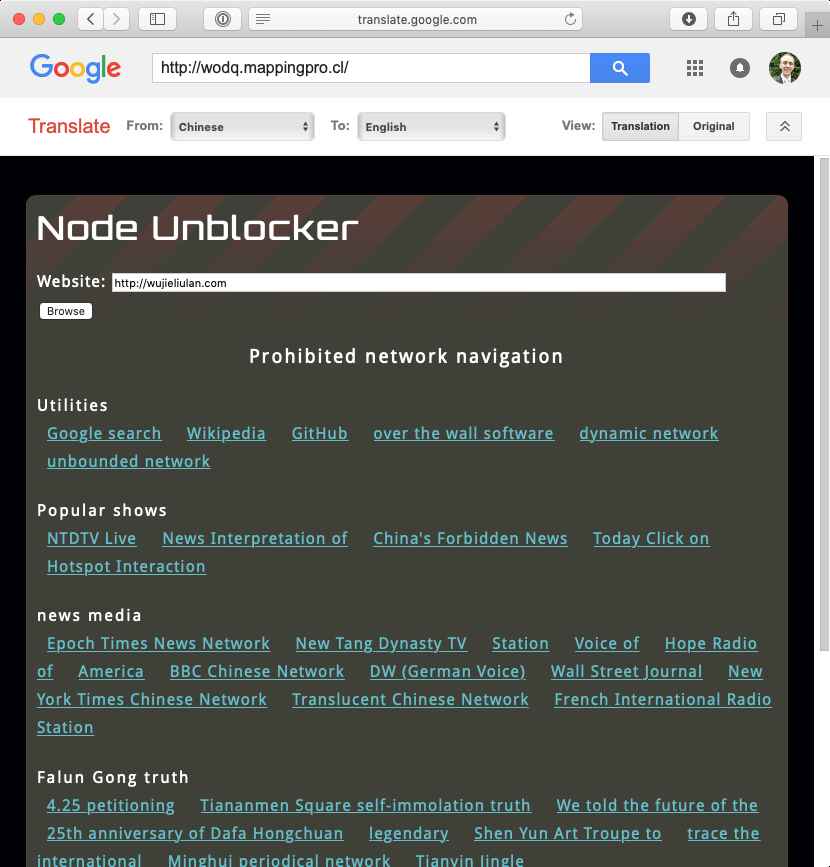
The page title mentions the Node Unblocker package, but the footer links to the GitHub project gfw-breaker/heroku-node-proxy. This appears to be an easily-deployable packaging of the former. The heroku-node-proxy repository links to what looks to be a Falun Gong news site.
Conclusion: an organisation is deploying Heroku instances provisioned with an implementation of Node Unblocker for censorship evasion, apparently in China. FreeDNS is used to recruit subdomains which provide access to nodes. Let's Encrypt is used to provide secure connections to these subdomains, though this feature is apparently not yet operational.